The Phishing Dojo
Simulate crypto security threats before they get you.
Real threats, real trainings.
The crypto industry loses millions to phishing, scams, and other threats every year.
Train to face them in The Phishing Dojo's most realistic scenarios.
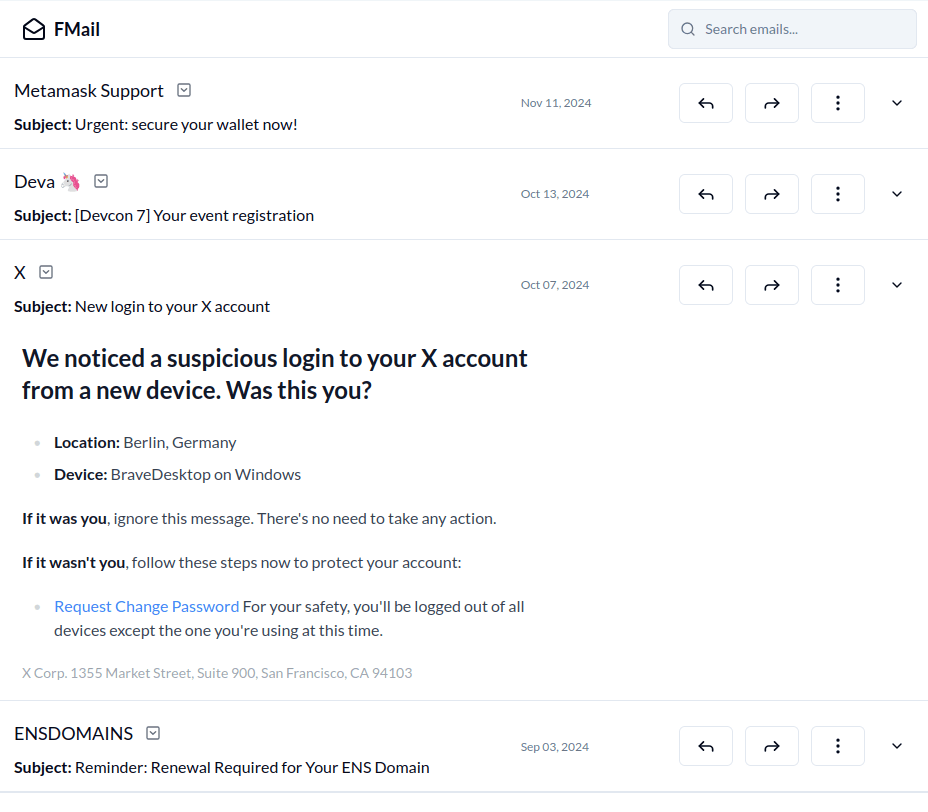
Phishing, Spam & Impersonation
Investigate emails with suspicious senders, headers, links and attachments.
Account & Transaction Spoofing
Explore block explorers to spot address spoofing, polluted transaction history, and other threats.

Fraudulent Signing Requests
From infinite approvals to token permits and obfuscated calldata: spot signing requests that'd drain all your funds.

Scam & Clone Sites
Detect fake websites designed to steal your passwords and private keys. Learn to identify fake domains, suspicious URLs, and spoofed interfaces.

Not enough? There's much more to come...
Start for free, today.
Realistic Simulations
First-hand experience authentic email clients, explorers, wallets and sites that look and feel real.
No Setup Needed
100% in-browser. No extensions, wallets, or additional software. Everything is safely contained.
Expert-Built Scenarios
Designed by security experts based on the latest threats targeting the crypto community.
Frequently asked questions
What is The Phishing Dojo?
The Phishing Dojo is a threat simulation platform designed to help crypto users identify and defend against social engineering, phishing, scams, and other notorious threats in the crypto ecosystem. Through realistic simulations and interactive training modules, we prepare you to recognize and avoid the tactics used by cybercriminals targeting you every day.
How can I get started with training?
The recommended way to get started is to sign up for a free account and start with the available trainings.
There's also free trainings with no signup required, although you'll need to signup to save your progress and access special trainings and more advanced features.
What types of security threats does the platform cover?
Phishing emails, fraudulent websites, wallet security (blind signing, infite approvals, token permits, obfuscated calldata), address spoofing, pollution of transaction history, look-alike tokens, and social engineering attacks. Each training module simulates real-world scenarios you might encounter in the crypto space.
We're rolling out new scenarios, trainings and features in the coming months, so make sure to sign up to get notified about new releases.
Do I need any tools like browser extensions, wallets, block explorers, etc?
No! You don't need to install anything nor ever leave The Phishing Dojo during the trainings. We've embedded email clients, websites, wallets, block explorers and more. All are safely contained within the platform, and look as realistic as possible.
I want to train my team - is there a business version?
Yes! We're starting to roll out a business version of The Phishing Dojo, featuring custom trainings, admin dashboards and dedicated team management and tracking features. Please contact us at hello@theredguild.org to learn more.
Still have questions? Email us at hello@theredguild.org